VSFTP:
Introduction
The File Transfer Protocol (FTP)
is used as one of the most common means of copying files between servers over
the Internet. Most web based download sites use the built in FTP capabilities
of web browsers and therefore most server oriented operating systems usually
include an FTP server application as part of the software suite. Linux is no
exception.
This chapter will show you how to
convert your Linux box into an FTP server using the default Very Secure FTP
Daemon (VSFTPD) package included in Fedora.
FTP Overview
FTP relies on a pair of TCP ports
to get the job done. It operates in two connection channels as I'll explain:
FTP Control Channel, TCP Port
21: All commands you send
and the ftp server's responses to those commands will go over the control
connection, but any data sent back (such as "ls" directory lists or
actual file data in either direction) will go over the data connection.
FTP Data Channel, TCP Port 20: This port is used for all subsequent data
transfers between the client and server.
In addition to these channels,
there are several varieties of FTP.
Types of FTP
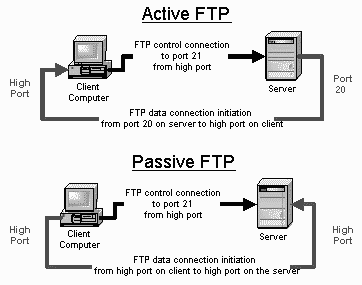
From a networking perspective,
the two main types of FTP are active and passive. In active FTP, the FTP server
initiates a data transfer connection back to the client. For passive FTP, the
connection is initiated from the FTP client. These are illustrated in Figure
15-1.
Figure 15-1 Active
And Passive FTP Illustrated
From a user management
perspective there are also two types of FTP: regular FTP in which files are
transferred using the username and password of a regular user FTP server, and
anonymous FTP in which general access is provided to the FTP server using a
well known universal login method.
Take a closer look at each type.
Active FTP
The sequence of events for active
FTP is:
- Your client connects to the FTP server by
establishing an FTP control connection to port 21 of the server. Your
commands such as 'ls' and 'get' are sent over this connection.
- Whenever the client requests data over the
control connection, the server initiates data transfer connections back to
the client. The source port of these data transfer connections is always
port 20 on the server, and the destination port is a high port (greater
than 1024) on the client.
- Thus the ls listing that you asked for comes
back over the port 20 to high port connection, not the port 21 control
connection.
FTP active mode therefore transfers
data in a counter intuitive way to the TCP standard, as it selects port 20 as
it's source port (not a random high port that's greater than 1024) and connects
back to the client on a random high port that has been pre-negotiated on the
port 21 control connection.
Active FTP may fail in cases
where the client is protected from the Internet via many to one NAT
(masquerading). This is because the firewall will not know which of the many
servers behind it should receive the return connection.
Passive FTP
Passive FTP works differently:
- Your client connects to the FTP server by
establishing an FTP control connection to port 21 of the server. Your
commands such as ls and get are sent over that connection.
- Whenever the client requests data over the
control connection, the client initiates the data transfer connections to
the server. The source port of these data transfer connections is always a
high port on the client with a destination port of a high port on the
server.
Passive FTP should be viewed as
the server never making an active attempt to connect to the client for FTP data
transfers. Because client always initiates the required connections, passive
FTP works better for clients protected by a firewall.
As Windows defaults to active
FTP, and Linux defaults to passive, you'll probably have to accommodate both
forms when deciding upon a security policy for your FTP server.
Regular FTP
By default, the VSFTPD package
allows regular Linux users to copy files to and from their home directories
with an FTP client using their Linux usernames and passwords as their login
credentials.
VSFTPD also has the option of
allowing this type of access to only a group of Linux users, enabling you to
restrict the addition of new files to your system to authorized personnel.
The disadvantage of regular FTP
is that it isn't suitable for general download distribution of software as
everyone either has to get a unique Linux user account or has to use a shared
username and password. Anonymous FTP allows you to avoid this difficulty.
Anonymous FTP
Anonymous FTP is the choice of
Web sites that need to exchange files with numerous unknown remote users.
Common uses include downloading software updates and MP3s and uploading
diagnostic information for a technical support engineers' attention. Unlike
regular FTP where you login with a preconfigured Linux username and password,
anonymous FTP requires only a username of anonymous and your email address for
the password. Once logged in to a VSFTPD server, you automatically have access
to only the default anonymous FTP directory (/var/ftp in the case of VSFTPD)
and all its subdirectories.
As seen in Chapter 6, "Installing Linux
Software", using anonymous FTP as a remote user is fairly straight
forward. VSFTPD can be configured to support user-based and or anonymous FTP in
its configuration file which you'll see later.
Problems With FTP And Firewalls
FTP frequently fails when the
data has to pass through a firewall, because firewalls are designed to limit
data flows to predictable TCP ports and FTP uses a wide range of unpredictable
TCP ports. You have a choice of methods to overcome this.
Note: The Appendix II, "Codes,
Scripts, and Configurations", contains examples of how to configure
the VSFTPD Linux firewall to function with both active and passive FTP.
Client Protected
By A Firewall Problem
Typically firewalls don't allow
any incoming connections at all, which frequently blocks active FTP from
functioning. With this type of FTP failure, the active FTP connection appears
to work when the client initiates an outbound connection to the server on port
21. The connection then appears to hang, however, as soon as you use the ls,
dir, or get commands. The reason is that the firewall is blocking the return
connection from the server to the client (from port 20 on the server to a high
port on the client). If a firewall allows all outbound connections to the
Internet, then passive FTP clients behind a firewall will usually work correctly
as the clients initiate all the FTP connections.
- Solution
Table 15-1 shows the general
rules you'll need to allow FTP clients through a firewall:
Table 15-1 Client
Protected by Firewall - Required Rules for FTP
|
Method |
Source Address |
Source Port |
Destination Address |
Destination Port |
Connection Type |
|
Allow outgoing control connections to server |
|||||
|
Control Channel |
FTP client / network |
High1 |
FTP server2 |
21 |
New |
|
FTP server2 |
21 |
FTP client/ network |
High |
Established3 |
|
|
Allow the client to establish data channels
to remote server |
|||||
|
Active FTP |
FTP server 2 |
20 |
FTP client / network |
High |
New |
|
FTP client / network |
High |
FTP server 2 |
20 |
Established3 |
|
|
Passive FTP |
FTP client / network |
High |
FTP server 2 |
High |
New |
|
FTP server 2 |
High |
FTP client / network |
High |
Established 3 |
|
1 Greater than 1024.
2 In some cases, you may want to allow all Internet users to have access,
not just a specific client server or network.
3 Many home-based firewall/routers automatically allow traffic for already
established connections. This rule may not be necessary in all cases.
Server Protected
By A Firewall Problem
Typically firewalls don't let any
connections come in at all. When a an incorrectly configured firewall protects
an FTP server, the FTP connection from the client doesn't appear to work at all
for both active and passive FTP.
- Solution
Table 15-2
outlines the general rules needed to allow FTP servers through a firewall.
|
Method |
Source Address |
Source Port |
Destination Address |
Destination Port |
Connection Type |
|
Allow incoming control connections to server |
|||||
|
Control Channel |
FTP client / network 2 |
High1 |
FTP server |
21 |
New |
|
FTP server |
21 |
FTP client / network 2 |
High |
Established3 |
|
|
Allow server to establish data channel to
remote client |
|||||
|
Active FTP |
FTP server |
20 |
FTP client / network 2 |
High |
New |
|
FTP client / network 2 |
High |
FTP server |
20 |
Established3 |
|
|
Passive FTP |
FTP client / network 2 |
High |
FTP server |
High |
New |
|
FTP server |
High |
FTP client / network 2 |
High |
Established 3 |
|
1 Greater than 1024.
2 In some cases, you may want to allow all Internet users to have access,
not just a specific client server or network.
3Many home-based firewall/routers automatically allow traffic for already
established connections. This rule may not be necessary in all cases.
How To Download And Install VSFTPD
Most Linux software products are
available in a precompiled package format. Downloading and installing packages
isn't hard. If you need a refresher, Chapter 6, "Installing Linux
Software", covers how to do this in detail. It is best to use the
latest version of VSFTPD.
When searching for the file,
remember that the VSFTPD packages' filename usually starts with the word vsftpd
followed by a version number, as in vsftpd-1.2.1-5.i386.rpm for Redhat/Fedora or vsftpd_2.0.4-0ubuntu4_i386.deb for Ubuntu.
How To Get VSFTPD Started
With Fedora, Redhat, Ubunbtu and
Debian You can start, stop, or restart VSFTPD after booting by using these
commands:
[root@bigboy tmp]# /etc/init.d/vsftpd start[root@bigboy tmp]# /etc/init.d/vsftpd stop[root@bigboy tmp]# /etc/init.d/vsftpd restart
With Redhat / Fedora you can
configure VSFTPD to start at boot you can use the chkconfig command.
[root@bigboy tmp]# chkconfig vsftpd on
With Ubuntu / Debian the
sysv-rc-conf command can be used like this:
root@u-bigboy:/tmp# sysv-rc-conf on
Note: In RedHat Linux version 8.0 and earlier, VSFTPD
operation is controlled by the xinetd process, which is covered in Chapter 16,
"Telnet, TFTP, and xinetd".
You can find a full description of how to configure these versions of Linux for
VSFTPD in Appendix III, "Fedora Version
Differences."
Testing the Status of VSFTPD
You can always test whether the
VSFTPD process is running by using the netstat -a command which lists all the
TCP and UDP ports on which the server is listening for traffic. This example
shows the expected output.
[root@bigboy root]# netstat -a | grep ftptcp 0 0 *:ftp *:* LISTEN[root@bigboy root]#
If VSFTPD wasn't running, there
would be no output at all.
The vsftpd.conf File
VSFTPD only reads the contents of
its vsftpd.conf configuration file only when it starts, so you'll have to
restart VSFTPD each time you edit the file in order for the changes to take
effect. The file may be located in either the /etc or the /etc/vsftpd directories depending on your Linux
distribution.
This file uses a number of
default settings you need to know about.
- VSFTPD runs as an anonymous FTP server.
Unless you want any remote user to log into to your default FTP directory
using a username of anonymous and a password that's the same as their
email address, I would suggest turning this off. The configuration file's
anonymous_enable directive can be set to no to disable this feature.
You'll also need to simultaneously enable local users to be able to log in
by removing the comment symbol (#) before the local_enable instruction.
- If you enable anonymous FTP with VSFTPD,
remember to define the root directory that visitors will visit. This is
done with the anon_root directive.
anon_root=/data/directory
- VSFTPD allows only anonymous FTP downloads to
remote users, not uploads from them. This can be changed by modifying the
anon_upload_enable directive shown later.
- VSFTPD doesn't allow anonymous users to
create directories on your FTP server. You can change this by modifying
the anon_mkdir_write_enable directive.
- VSFTPD logs FTP access to the
/var/log/vsftpd.log log file. You can change this by modifying the
xferlog_file directive.
- By default VSFTPD expects files for anonymous
FTP to be placed in the /var/ftp directory. You can change this by
modifying the anon_root directive. There is always the risk with anonymous
FTP that users will discover a way to write files to your anonymous FTP
directory. You run the risk of filling up your /var partition if you use
the default setting. It is best to make the anonymous FTP directory reside
in its own dedicated partition.
The configuration file is fairly
straight forward as you can see in the snippet below where we enable anonymous
FTP and individual accounts simultaneously.
# Allow anonymous FTP?anonymous_enable=YES...# The directory which vsftpd will try to change# into after an anonymous login. (Default = /var/ftp)anon_root=/data/directory...# Uncomment this to allow local users to log in.local_enable=YES...# Uncomment this to enable any form of FTP write command.# (Needed even if you want local users to be able to upload files)write_enable=YES...# Uncomment to allow the anonymous FTP user to upload files. This only# has an effect if global write enable is activated. Also, you will# obviously need to create a directory writable by the FTP user.#anon_upload_enable=YES...# Uncomment this if you want the anonymous FTP user to be able to create# new directories.#anon_mkdir_write_enable=YES...# Activate logging of uploads/downloads.xferlog_enable=YES...# You may override where the log file goes if you like.# The default is shown below.xferlog_file=/var/log/vsftpd.log...
To activate or deactivate a feature,
remove or add the # at the beginning of the appropriate line.
Other vsftpd.conf Options
There are many other options you
can add to this file:
- Limiting the maximum number of client
connections (max_clients)
- Limiting the number of connections by source
IP address (max_per_ip)
- The maximum rate of data transfer per
anonymous login. (anon_max_rate)
- The maximum rate of data transfer per
non-anonymous login. (local_max_rate)
Descriptions on this and more can
be found in the vsftpd.conf man pages.
FTP Security Issues
FTP has a number of security
drawbacks, but you can overcome them in some cases. You can restrict an
individual Linux user's access to non-anonymous FTP, and you can change the
configuration to not display the FTP server's software version information, but
unfortunately, though very convenient, FTP logins and data transfers are not
encrypted.
The /etc/vsftpd.ftpusers File
For added security, you may
restrict FTP access to certain users by adding them to the list of users in the
/etc/vsftpd.ftpusers file. The VSFTPD package creates this file with a number
of entries for privileged users that normally shouldn't have FTP access. As FTP
doesn't encrypt passwords, thereby increasing the risk of data or passwords
being compromised, it is a good idea to let these entries remain and add new
entries for additional security.
Anonymous Upload
If you want remote users to write
data to your FTP server, then you should create a write-only directory within
/var/ftp/pub. This will allow your users to upload but not access other files
uploaded by other users. The commands you need are:
[root@bigboy tmp]# mkdir /var/ftp/pub/upload[root@bigboy tmp]# chmod 722 /var/ftp/pub/upload
FTP Greeting Banner
Change the default greeting
banner in the vsftpd.conf file to make it harder for malicious users to
determine the type of system you have. The directive in this file is.
ftpd_banner= New Banner Here
Using SCP As
Secure Alternative To FTP
One of the disadvantages of FTP
is that it does not encrypt your username and password. This could make your
user account vulnerable to an unauthorized attack from a person eavesdropping
on the network connection. Secure Copy (SCP) and Secure FTP (SFTP) provide
encryption and could be considered as an alternative to FTP for trusted users.
SCP does not support anonymous services, however, a feature that FTP does
support.
Troubleshooting FTP
You should always test your FTP
installation by attempting to use an FTP client to log in to your FTP server to
transfer sample files.
The most common sources of
day-to-day failures are incorrect usernames and passwords.
Initial setup failures could be
caused by firewalls along the path between the client and server blocking some
or all types of FTP traffic. Typical symptoms of this are either connection
timeouts or the ability to use the ls command to view the contents of a
directory without the ability to either upload or download files. Follow the
firewall rule guidelines to help overcome this problem. Connection problems
could also be the result of typical network issues outlined in Chapter 4,
"Simple Network
Troubleshooting".
Tutorial
FTP has many uses, one of which
is allowing numerous unknown users to download files. You have to be careful,
because you run the risk of accidentally allowing unknown persons to upload
files to your server. This sort of unintended activity can quickly fill up your
hard drive with illegal software, images, and music for the world to download,
which in turn can clog your server's Internet access and drive up your
bandwidth charges.
FTP Users with
Only Read Access to a Shared Directory
In this example, anonymous FTP is
not desired, but a group of trusted users need to have read only access to a
directory for downloading files. Here are the steps:
1) Disable anonymous FTP. Comment
out the anonymous_enable line in the vsftpd.conf file like this:
# Allow anonymous FTP?anonymous_enable=NO
2) Enable individual logins by
making sure you have the local_enable line uncommented in the vsftpd.conf file
like this:
# Uncomment this to allow local users to log in.local_enable=YES
3) Start VSFTP.
[root@bigboy tmp]# service vsftpd start
4) Create a user group and shared
directory. In this case, use /home/ftp-users and a user group name of ftp-users
for the remote users
[root@bigboy tmp]# groupadd ftp-users[root@bigboy tmp]# mkdir /home/ftp-docs
5) Make the directory accessible
to the ftp-users group.
[root@bigboy tmp]# chmod 750 /home/ftp-docs[root@bigboy tmp]# chown root:ftp-users /home/ftp-docs
6) Add users, and make their
default directory /home/ftp-docs
[root@bigboy tmp]# useradd -g ftp-users -d /home/ftp-docs user1[root@bigboy tmp]# useradd -g ftp-users -d /home/ftp-docs user2[root@bigboy tmp]# useradd -g ftp-users -d /home/ftp-docs user3[root@bigboy tmp]# useradd -g ftp-users -d /home/ftp-docs user4[root@bigboy tmp]# passwd user1[root@bigboy tmp]# passwd user2[root@bigboy tmp]# passwd user3[root@bigboy tmp]# passwd user4
7) Copy files to be downloaded by
your users into the /home/ftp-docs directory
8) Change the permissions of the
files in the /home/ftp-docs directory for read only access by the group
[root@bigboy tmp]# chown root:ftp-users /home/ftp-docs/*[root@bigboy tmp]# chmod 740 /home/ftp-docs/*
Users should now be able to log in via FTP to the server using their new
usernames and passwords. If you absolutely don't want any FTP users to be able
to write to any directory, then you should set the write_enable line in your
vsftpd.conf file to no:
write_enable = NO
Remember, you must restart VSFTPD
for the configuration file changes to take effect.
Sample Login
Session To Test Functionality
Here is a simple test procedure
you can use to make sure everything is working correctly:
1) Check for the presence of a
test file on the ftp client server.
[root@smallfry tmp]# lltotal 1-rw-r--r-- 1 root root 0 Jan 4 09:08 testfile[root@smallfry tmp]#
2) Connect to bigboy via FTP
[root@smallfry tmp]# ftp 192.168.1.100Connected to 192.168.1.100 (192.168.1.100)220 ready, dude (vsFTPd 1.1.0: beat me, break me)Name (192.168.1.100:root): user1331 Please specify the password.Password:230 Login successful. Have fun.Remote system type is UNIX.Using binary mode to transfer files.ftp>
As expected, we can't do an upload transfer of testfile to bigboy.
ftp> put testfilelocal: testfile remote: testfile227 Entering Passive Mode (192,168,1,100,181,210)553 Could not create file.ftp>
But we can view and download a copy of the VSFTPD RPM located on the FTP
server bigboy.
ftp> ls227 Entering Passive Mode (192,168,1,100,35,173)150 Here comes the directory listing.-rwxr----- 1 0 502 76288 Jan 04 17:06 vsftpd-1.1.0-1.i386.rpm226 Directory send OK.ftp> get vsftpd-1.1.0-1.i386.rpm vsftpd-1.1.0-1.i386.rpm.tmplocal: vsftpd-1.1.0-1.i386.rpm.tmp remote: vsftpd-1.1.0-1.i386.rpm227 Entering Passive Mode (192,168,1,100,44,156)150 Opening BINARY mode data connection for vsftpd-1.1.0-1.i386.rpm (76288 bytes).226 File send OK.76288 bytes received in 0.499 secs (1.5e+02 Kbytes/sec)ftp> exit221 Goodbye.[root@smallfry tmp]#
As expected, anonymous FTP fails.
[root@smallfry tmp]# ftp 192.168.1.100Connected to 192.168.1.100 (192.168.1.100)220 ready, dude (vsFTPd 1.1.0: beat me, break me)Name (192.168.1.100:root): anonymous331 Please specify the password.Password:530 Login incorrect.Login failed.ftp> quit221 Goodbye.[root@smallfry tmp]#
Now that testing is complete, you
can make this a regular part of your FTP server's operation.
Conclusion
FTP is a very useful software
application that can have enormous benefit to a Web site or to collaborative
computing in which files need to be shared between business partners. Although
insecure, it is universally accessible, because FTP clients are a part of all
operating systems and Web browsers. If data encryption security is of great
importance to you, then you should probably consider SCP as a possible alternative.
You can find more information on it in Chapter 17, "Secure
Remote Logins and File Copying".
Retrieved from
"http://www.linuxhomenetworking.com/wiki/index.php/Quick_HOWTO_:_Ch15_:_Linux_FTP_Server_Setup"